Leaked NSA Report Is Short on Facts, Proves Little in ‘Russiagate’ Case
The document allegedly leaked by whistleblower Reality Winner reinforces assertions made by President Trump that the Russia story is fake news.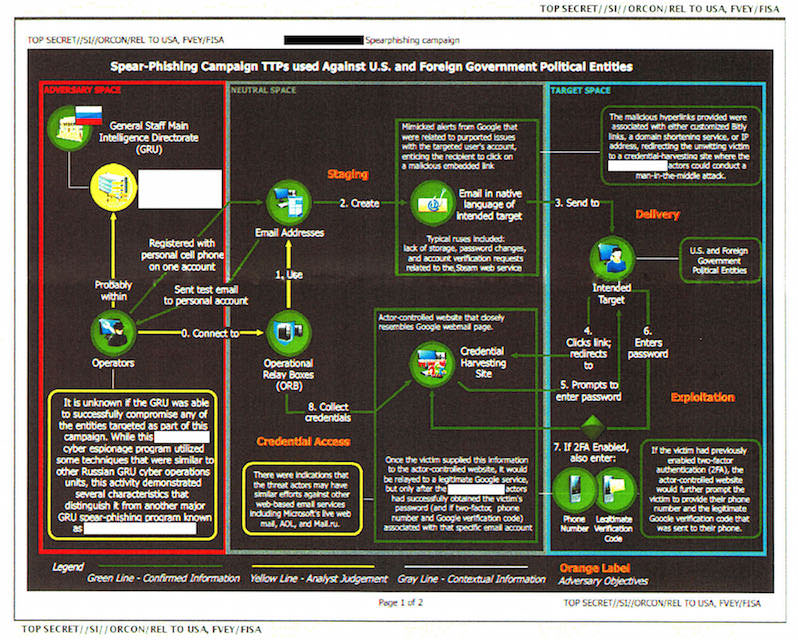 The chart from the NSA document that allegedly was leaked by Reality Winner. (The Intercept)
The chart from the NSA document that allegedly was leaked by Reality Winner. (The Intercept)
The chart from the NSA document that allegedly was leaked by Reality Winner. (The Intercept)
By all accounts, Reality Leigh Winner is an intelligent, committed professional who served for six years in the U.S. Air Force as a Farsi and Pashto linguist, specializing in communications intercept operations and analysis conducted on behalf of the National Security Agency (NSA). She left the Air Force in 2016 and in February started working as a civilian contractor at the Georgia Cryptologic Center, an NSA facility in Augusta, Ga., that specializes in analyzing communications intercepts originating in Europe, the Middle East and North Africa.
Sometime in early May, Winner reportedly accessed a top-secret NSA analysis detailing intelligence on Russian cyberactivity targeting the 2016 U.S. presidential election. Media reports indicate that Winner, prior to starting her new job, had an extensive social media presence, with numerous posts critical of Donald Trump and expressing fury over his repeated minimization of alleged Russian electoral interference. The NSA document details specific cyberattack activities attributed to actors working on behalf of the Russian military’s Main Intelligence Directorate (Glavnoye Razvedyvatel’noye Upravleniye, or GRU).
Winner, perhaps emboldened by the recent spate of highly classified leaks related to allegations of collusion between the Trump administration and Russia, allegedly made the unfortunate (and illegal) decision to anonymously mail a copy of the highly classified document to The Intercept, an online magazine that specializes in publishing leaked material. U.S. government investigators reportedly uncovered her responsibility for the leak, and Winner was arrested.
She now faces up to 10 years in prison. It is not known whether Winner feels that the potential consequences of her actions were worth the effort.
The release of the document has invigorated the Russian hacking hysteria before former FBI Director James Comey’s much-ballyhooed testimony before Congress. The issue of Russian meddling is expected to be a prominent focus of the Comey hearing, with significant attention placed on the role of the GRU in orchestrating the events detailed in the report. But upon closer scrutiny, the NSA document allegedly leaked by Winner reinforces assertions made by President Trump that the Russia story is fake news.
The NSA document—titled “Russia/Cybersecurity: Main Intelligence Directorate Actors [Redacted] Target U.S. Companies and Local U.S. Government Officials Using Voter Registration-Themed Emails, Spoof Election-Related Products and Services, Research Absentee Ballot Email Addresses; August to November 2016”—provides, on its face, a damning indictment of the Russians. Following in the footsteps of the Dec. 29, 2016, White House statement announcing sanctions targeting Russia, and the CIA-FBI-NSA joint national intelligence assessment on Russia’s influence campaign targeting the 2016 election, the NSA analysis makes blanket assertions of the involvement of the Russian GRU in the cyberattack on the election.
The opening paragraph of the leaked NSA document states:
Russian General Staff Main Intelligence Directorate actors … executed cyber espionage operations against a named U.S. company in August 2016, evidently to obtain information on elections-related software and hardware solutions. … The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting U.S. local government organizations.
Two explanatory footnotes, heavily redacted, likewise attribute the reported actions of “Cyber threat actors” to the GRU and other redacted organizations affiliated with it. There is no doubt that, from the perspective of NSA analysts who prepared the document, the GRU was the driving force behind the cyberactivities being reported.
The strength of this assertion, however, collapses when one examines the colored chart that accompanied the text of the report detailing the “Spear-Phishing Campaign TTPs used Against U.S. and Foreign Government Entities” (TTPs are tactics, techniques and procedures). While the document, as released by The Intercept, shows only the first page of what is described as a two-page chart, the material it contains is clear and concise regarding what it is illustrating. The activity flow chart, which details the sequencing and relationships involved in the execution of the spear-phishing campaign, breaks the sourcing of the information into three categories: green, yellow and gray.
Green stands for “confirmed information.” Most of the technical details reported on fall into this category.
Yellow represents what is described as an “analyst judgment,” which is a far cry from the assertion of fact indicated by the green designation. The color yellow is used five times. Three signify the flow of activity involved in the TPPs. Two, however, deal with the critical issue of attribution. While the report indicates that the “operators” (cyberactors) are confirmed quantities, the linkage between them and their immediate supervising command authority is not confirmed, but rather derived from an analytical judgment.
This is a critical fact that has been overlooked in the media hype surrounding the NSA document. It is also significant that this command authority is not the GRU headquarters itself, but rather a different entity, whose identity has been redacted throughout the document by The Intercept at the request of the NSA. The NSA document provides some clues as to the affiliation of the entity in question, noting that it is similar to “other Russian GRU Cyber Operations Units.”
There is little doubt that the NSA has a specific unit in mind, and that its identity is so sensitive that the agency requested The Intercept to redact it throughout the document. It is also clear, however, that the NSA has not established a confirmed link between this secret cyberoperations unit and the “operators” behind the reported cyberoperations targeting the 2016 election. Rather, the link is purely speculative, a product of analytical judgment, not hard fact.
The third and final color used in the NSA chart is gray, which stands for “contextual information.” This color is used three times in the chart. First, it links the confirmed activity to other cyberattacks on “U.S. and Foreign Government Political Entities.” What is important in this revelation is that the NSA is declaring that it has no proof that the events documented in the leaked document have any connection with, for instance, the cyberattack on the Democratic National Committee (DNC), the German Parliament or any other entity. An analytical assumption is being made that is provided for “context.” But the document does not sustain this assumption with any fact-based data.
The second use of “contextual information” deals with a specific type of operation known as “credential harvesting,” in which passwords, phone numbers and verification codes are collected using what is called a “man in the middle” attack—basically diverting the signal to a host server, where the harvesting is done, before sending it on to its intended destination. The chart indicates that the NSA can confirm credential harvesting at an “actor controlled” server based in what is called “neutral space”—neither Russia (“adversary space”) nor the United States (“target space”)—most likely a server on European soil. It hints at a capability to harvest credentials in the “target space,” but the link is gray—for context only. There is no fact-based information that allows such an assertion to be made.
The third and final use of “contextual information” deals with the attribution to the GRU itself. The chart links the GRU to the redacted cyberentity using a gray line (the redacted entity had, in turn, been linked to the “confirmed” operators in yellow). The significance of this attribution is enormous—the NSA is acknowledging that any attribution of the GRU to the activities being reported on is purely “contextual” in nature. It has no evidence of this attribution whatsoever.
Nothing in the document’s confirmed information links it to the GRU. The GRU attribution is presented for contextual purposes only. It is an inferred command relationship to a redacted cyberoperations management capability that is linked to the confirmed cyberoperators only through analysis (i.e., best guess), not fact.
The NSA document, both in its title and text, is therefore misleading in the extreme. There is simply no fact-based information provided in the report that confirms that the events reported on were being organized and managed by the Russian GRU, despite the document’s assertions otherwise.
This lack of confirmation of any fact-based linkage between the GRU and the cyberattacks on the 2016 election in the NSA document is striking in another regard. The NSA has always been assumed to be the agency that possessed “smoking gun” evidence when it came to Russian attribution in the cyberattacks on the American electoral process.
The CIA-FBI-NSA joint assessment on Russia’s alleged influence campaign claims that Russian activity was twofold. The first, carried out by an entity known as “Advanced Persistent Threat (APT) 29,” or “Fancy Bear,” has been attributed to the Russian Federal Security Service (Federalnaya Sluzhba Bezopasnosti, or FSB). This attack began in July 2015 and continued through at least June 2016. It has been characterized as a classic information-gathering exercise of the sort affiliated with the classic espionage mission of an intelligence service.
The second attack of prime interest attributed to the GRU involved an entity known as “APT 28,” or “Cozy Bear.” This attack began in March 2016 and continued through May 2016, when, allegedly, a significant amount of data was stolen and made public through an online entity known as “Guccifer 2.0” and a variety of web-based publishers, including DCLeaks and WikiLeaks. It is the theft and use of stolen information by APT 28 in an effort to influence the outcome of the 2016 election that U.S. officials find so galling, which is why the GRU has been singled out for attribution and blame.
President Obama issued an amended executive order on Dec. 29, 2016, that sanctioned the GRU and FSB, along with four senior GRU officers and three companies that allegedly provided material support to the GRU. The combination of the president’s sanctions and the declassified findings of the CIA-FBI-NSA joint assessment helped create an air of finality regarding attribution of the cyberattack to the GRU. This attribution has not been challenged, either by the mainstream media or Congress.
Contrary to repeated assertions by well-compensated talking heads on cable news, there is no unified consensus by “all 17 agencies” of the U.S. intelligence community on Russian “meddling” with the 2016 election. Only three agencies weighed in on the Russian assessment—the CIA, the FBI and the NSA.
The CIA’s contribution appears to be purely speculative. It is limited to recycling a 2012 open-source assessment of Russian media-based propaganda to sustain the 2016 allegations of Russian meddling in the 2016 election.
The FBI’s contribution to the report was supposedly more forensically based, derived from data attributed to the server used by the Democratic National Committee and as such deemed particularly damning when it came to attribution to APT 28, the GRU. The main problem with the FBI’s assertion, however, is that it was not based upon an independent forensic examination of the DNC server by FBI agents, but rather the independent assessments of a private cybersecurity company, CrowdStrike, contracted by the DNC to investigate the March 2016 cyberintrusion into its servers.
CrowdStrike quickly assessed that the cyberattack had been carried out by APT 28 and named the Russian GRU as the culprit, a finding shared with The Washington Post, which published the assertion. This CrowdStrike-driven APT 28-GRU linkage has been accepted without question ever since (it should be noted that a similar CrowdStrike assessment linking APT 28 and the GRU to cyberactivity in the Ukraine has been discredited, significantly diluting the credibility of this company’s analysis).
The DNC mysteriously denied the FBI direct access to its servers, leaving the agency no option but to limit its investigation to the data provided by CrowdStrike. The CrowdStrike data, however, provides no conclusive forensic link to Russia or the GRU with regard to the cyberattack on the DNC server. Moreover, there is good reason to believe that CrowdStrike is the only source of information linking the APT 28 “Cozy Bear” intrusion to the DNC.
Even after information from the DNC was made public by WikiLeaks, no action was taken to alert Hillary Clinton campaign Chairman John Podesta that his personal emails had been stolen. This indicates that neither the FBI nor the NSA were aware of that particular intrusion. The FBI didn’t interview Podesta about the breach until Oct. 9, 2016—two days after WikiLeaks published the initial batch of his emails.
Likewise, none of the victims of the cyberattacks detailed in the NSA document leaked allegedly by Winner had been alerted about the APT 28-GRU attacks. This reinforces the notion that the specific attribution of the Russian GRU to the DNC cyberintrusion is solely the product of flawed and rushed analysis by a private cybersecurity firm on the payroll of the DNC, and not the independent assessment of either the FBI or NSA.
The classification markings on the NSA document allegedly leaked by Winner likewise provide clues as to the dearth of forensic data available to the U.S. intelligence community when it comes to attributing the GRU-APT 28 to cyberattacks on the American electoral process. The information clearly is derived from the interception of internet activity—the body of the report focuses on the use of Google by the cyberoperators as the vector for their spear-phishing efforts.
According to documents leaked by Edward Snowden, the sole source of collection against Google Cloud connectivity between Europe (i.e., “neutral space”) and the United States (i.e., “target space”) is through a program known as “Muscular,” which taps into four T16 communication cables at a London-based commercial facility referred to as DS-200B. Muscular is run by the British equivalent of the NSA, known as the Government Communications Headquarters, or GCHQ.
The classification markings on the NSA document leaked by Winner indicate that it is “originator controlled” (i.e., a foreign source) that has been released to the United States via protocols that comply with the requirements of the Foreign Intelligence Surveillance Act, or FISA. The only source for collection against European-based Google Cloud data is the GCHQ-run Muscular operation.
However, in order for this data to be released to the NSA for subsequent analysis using a separate U.S.-based system, known as “Turmoil,” it would have to confirm the requirements of FISA Act 702, governing the collection of communications intelligence from foreign sources. The presence of the FISA marking indicates that, with regard to the data collected in the NSA document, this is the case.
The contents of the NSA document, together with its security markings, strongly suggest that this represents the first significant independent analysis by an American intelligence agency of data linked to activity attributed by to APT 28-GRU. Neither the CrowdStrike data covering the March-April 2016 DNC cyberattack nor the hacking of Podesta’s email server was covered as a collection requirement by either the FBI or NSA. Muscular apparently did not detect the 2016 DNC attack, and the Podesta event simply involved hacked emails.
The GCHQ data collected under Muscular and released to the NSA through FISA channels for processing via the Turmoil system, which was subsequently published in the leaked NSA document, represents the most up-to-date intelligence available on the alleged Russian cyberattack on the 2016 election. It benefits from the collective insight derived from all previously collected intelligence on hostile cyberintrusions into the American electoral system in 2016. And it does not directly implicate, with confirmed fact, either the Russian government or the GRU.
The consequences of the dearth of fact-based intelligence linking the GRU to meddling in the 2016 election are many. It exposes the decision by President Obama to single out the GRU for sanctions last December as fraudulent in nature and politically motivated, since it sustained an attribution by CrowdStrike that was not founded in hard fact, but rather paid for by DNC dollars.
It also reveals the CIA-FBI-NSA joint assessment as being fundamentally flawed, calling into question the credibility of James Clapper (the former director of national intelligence), John Brennan (the former director of the CIA), Mike Rogers (the current director of NSA) and James Comey (the former director of the FBI) when it comes to the investigation into the allegations of Russian meddling in the 2016 election. All four men have testified extensively before various congressional committees, and will more than likely be called upon to testify again and again, in what has become an endless inquisition, the premise of which has at least partially been exposed as lacking a factual basis.
The perpetrators of the “Russia did it” line of attack—including the Democratic members of the House and Senate Intelligence Committees, who are in a position to know better due to their exposure to raw NSA intelligence of the sort used to underpin the analysis in the NSA document leaked by Winner—have hidden behind a veil of secrecy when it comes to protecting the sources used to sustain their assertions that the Russian government and Russian intelligence services (in particular, the GRU) were involved in meddling in the domestic political affairs of the United States.
These assertions have been repeated without attribution and reinforced by well-timed leaks of unverified information by anonymous sources to an unquestioning media until they have been endorsed as unquestioned fact.
By allegedly leaking a highly classified NSA document, Winner has provided the American public with its first unvarnished look at what the true state of affairs is regarding the specific intelligence underpinning one of the foundational accusations that have been leveled against Russia today. In short, there is no quality intelligence that implicates the GRU as being behind the APT 28-“Cozy Bear” cyberattacks on the DNC and American electoral system. The Russian threat has been exposed as a phantom menace.
It can now be clearly shown that any such attribution is purely speculative in nature, derived from the politically motivated and fundamentally flawed analysis conducted by a private company, CrowdStrike, which was subsequently adopted by the FBI before becoming a part of a national narrative that has been placed out of bounds when it comes to serious inquiry by a media that seems to have forgotten its responsibility to report fact-based truth, regardless of consequence.
In many ways, the rush to blame Russia for attempting to undermine American democracy by meddling in our election system has become a self-fulfilling prophesy. The damage done to the credibility of our democratic institutions as a result of the politicized congressional proceedings has been incalculable, and by all accounts the worst is yet to come.
The Russians barely had to lift a finger—the wounds derived from this political maelstrom have all been self-inflicted. The fact that the mainstream media have been unable to accurately report on the issue only underscores the depths to which institutions and agencies will fall to deride and destroy that which they detest and abhor, namely President Trump
The anti-Trump movement may yet cripple or even bring down his presidency (with no small amount of help being provided by the president himself, through his words, actions and tweets). Such a victory, if and when it comes, however, will probably prove to be a Pyrrhic one for Trump’s many opponents. After putting so much capital into accusing Russia and the GRU in meddling in American domestic political affairs—and, by extension, accusing the president of colluding with the Russians in this endeavor—the Democrats had better be able to back up their claims with unassailable, fact-based information. Based upon a close examination of the NSA’s latest analysis, courtesy of the document being linked to Winner, this intelligence does not exist.
Your support matters…Independent journalism is under threat and overshadowed by heavily funded mainstream media.
You can help level the playing field. Become a member.
Your tax-deductible contribution keeps us digging beneath the headlines to give you thought-provoking, investigative reporting and analysis that unearths what's really happening- without compromise.
Give today to support our courageous, independent journalists.






You need to be a supporter to comment.